There may be two new areas of attack for malformed WMF files, which
may not be covered by MS06-001? So far, no exploits in the wild have
been reported and I am watching this new potential exposure.
Microsoft Windows Graphics Rendering Engine Multiple Memory Corruption
Vulnerabilities
http://www.incidents.org/diary.php?storyid=1031http://www.securityfocus.com/bid/16167/infoQUOTE: Microsoft Windows WMF graphics rendering engine is affected by
multiple memory corruption vulnerabilities. These issues affect the
'ExtCreateRegion' and 'ExtEscape' functions. These problems present
themselves when a user views a malicious WMF formatted file containing
specially crafted data. Reports indicate that these issues lead to a
denial of service condition, however, it is conjectured that arbitrary
code execution is possible as well. Any code execution that occurs
will be with the privileges of the user viewing a malicious image. An
attacker may gain SYSTEM privileges if an administrator views the
malicious file.
But let us stay calm as it is not 100% sure yet, that we will have a new problem.
The time was too short for me to look into this very closely.
Microsoft official response to today's Bugtraq disclosure will be posted shortly at:
http://blogs.technet.com/msrc/
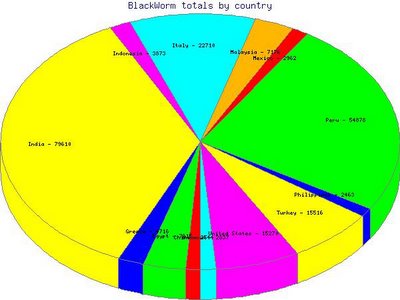 The real exact infection number counter seems to be around 300.000 infections at this moment. The pie chart shows the total infections by country for all countries with greater than 2000 infected IP addresses. The high infection rates in India, Peru and Italy are interesting to note. It is possible some of these figures are not 100% correct, but I do believe India is the hardest-hit country by far in terms of overall infection rate. Even so, 300.000 infected users worldwide is not a terribly large amount when compared to previous worms like Sober or Mydoom. And like I told you before Belgium and the Netherlands got just a few hundreds of infections. However, with this worm it isn't the quantity of infected users, it is the destructive payload which is most concerning.
The real exact infection number counter seems to be around 300.000 infections at this moment. The pie chart shows the total infections by country for all countries with greater than 2000 infected IP addresses. The high infection rates in India, Peru and Italy are interesting to note. It is possible some of these figures are not 100% correct, but I do believe India is the hardest-hit country by far in terms of overall infection rate. Even so, 300.000 infected users worldwide is not a terribly large amount when compared to previous worms like Sober or Mydoom. And like I told you before Belgium and the Netherlands got just a few hundreds of infections. However, with this worm it isn't the quantity of infected users, it is the destructive payload which is most concerning.


